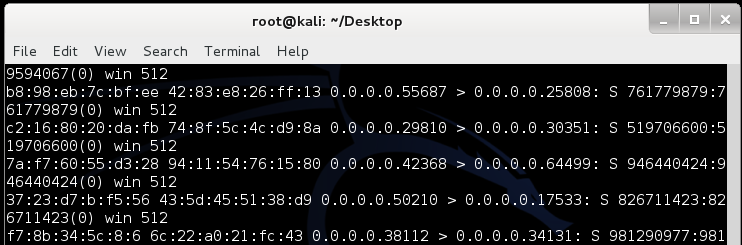
Gratuitous ARP and Basics of Connecting a Cisco IOS Switch with a Cisco CatOS Switch | HumairAhmed.com

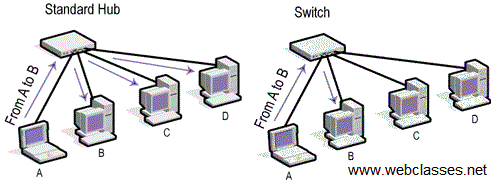
Types of Cisco Switches > Implementing Cisco IP Switched Networks (SWITCH) Foundation Learning Guide: Network Design Fundamentals | Cisco Press
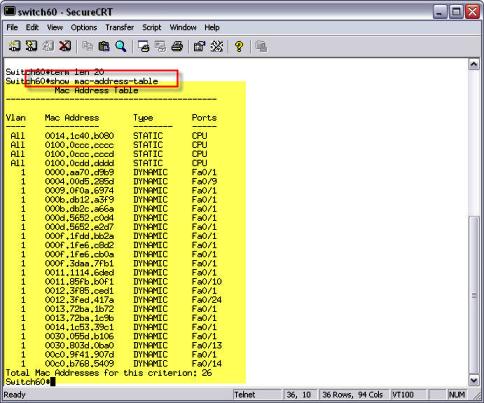
Main Network Hardware's Difference: Integrated Devices, Router, Network Switch & Firewall – Router Switch Blog

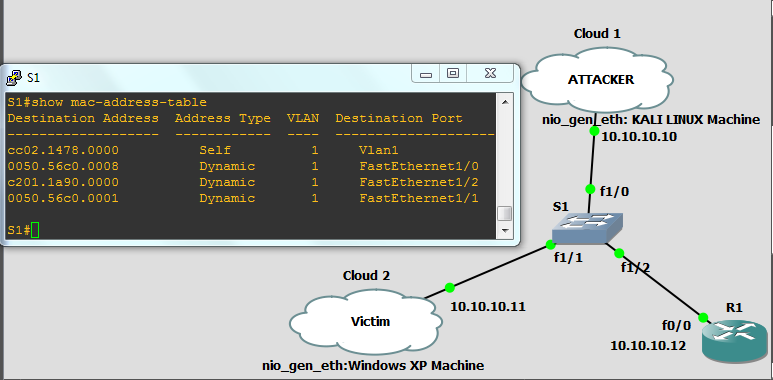



![How the switch uses the CAM tables - Python Penetration Testing Essentials [Book] How the switch uses the CAM tables - Python Penetration Testing Essentials [Book]](https://www.oreilly.com/api/v2/epubs/9781789138962/files/assets/4f76d848-e99f-42e0-b0e0-38b7d139b0df.png)