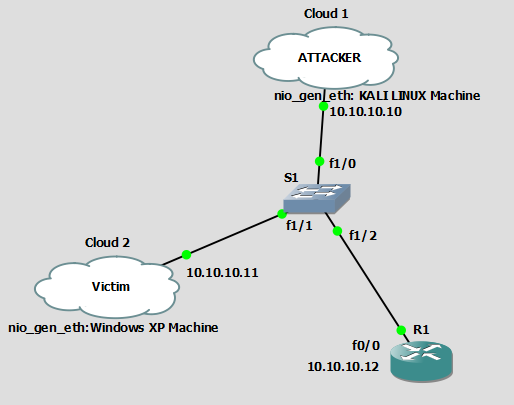
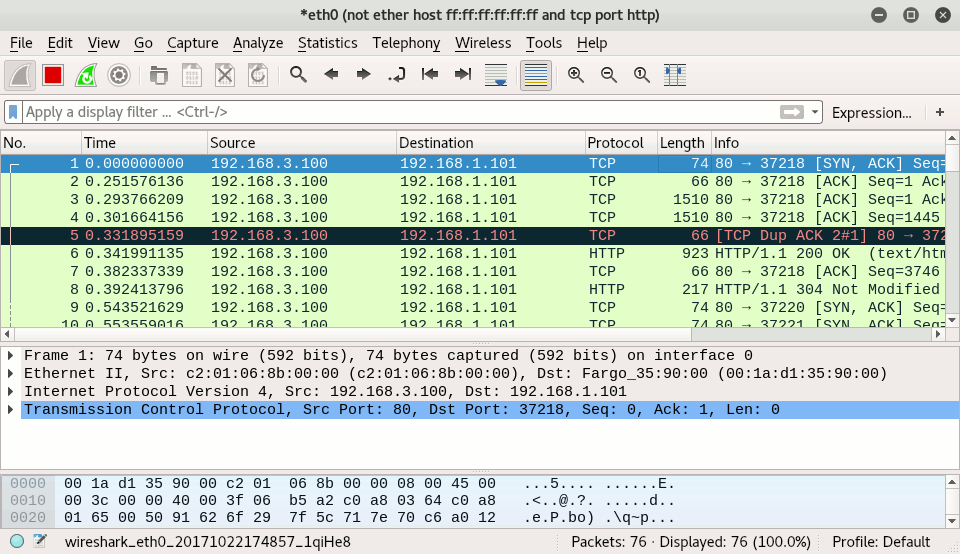
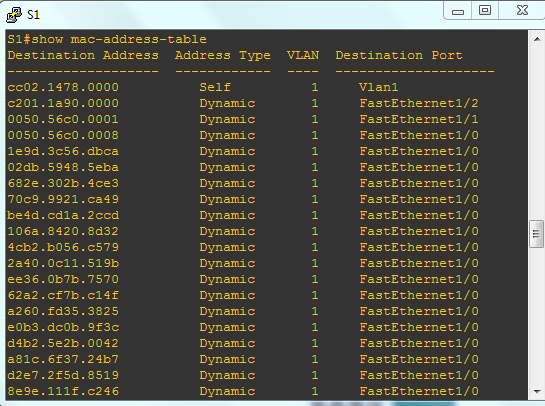
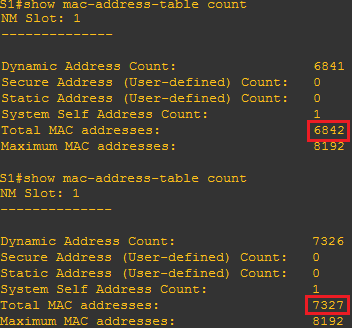
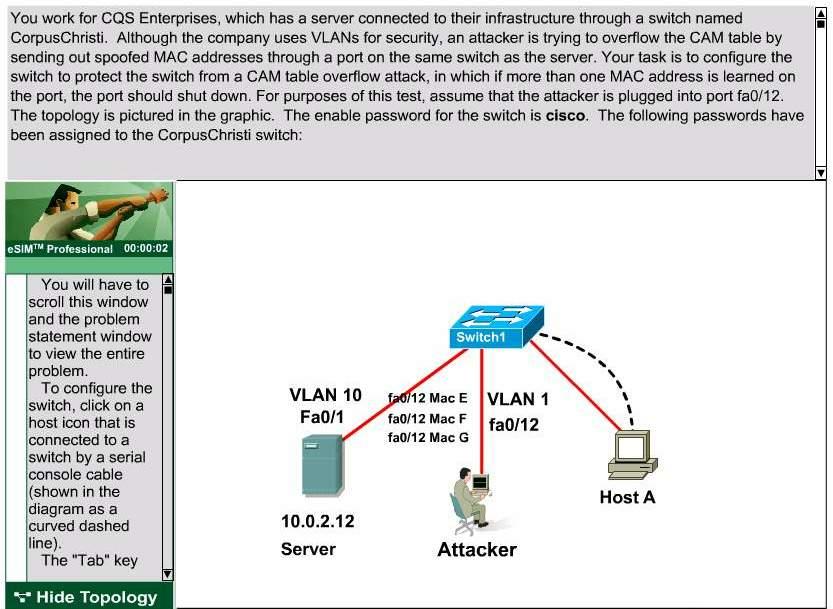
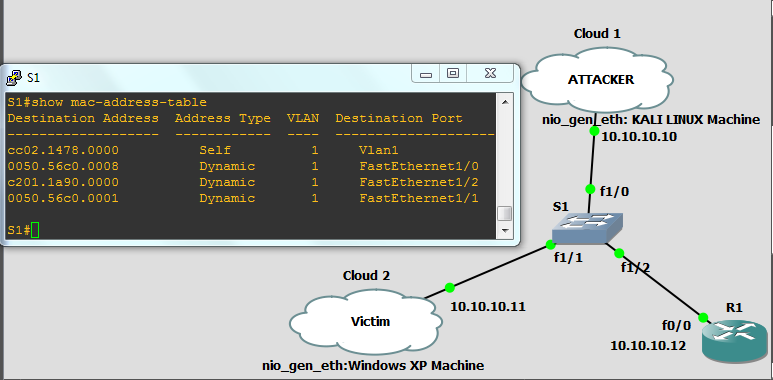
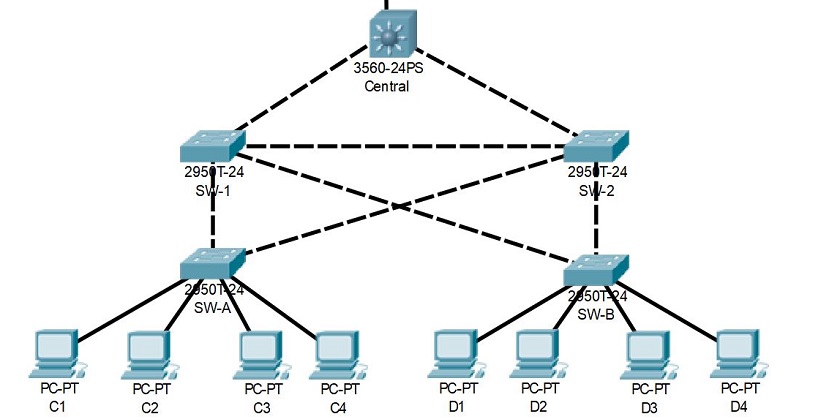
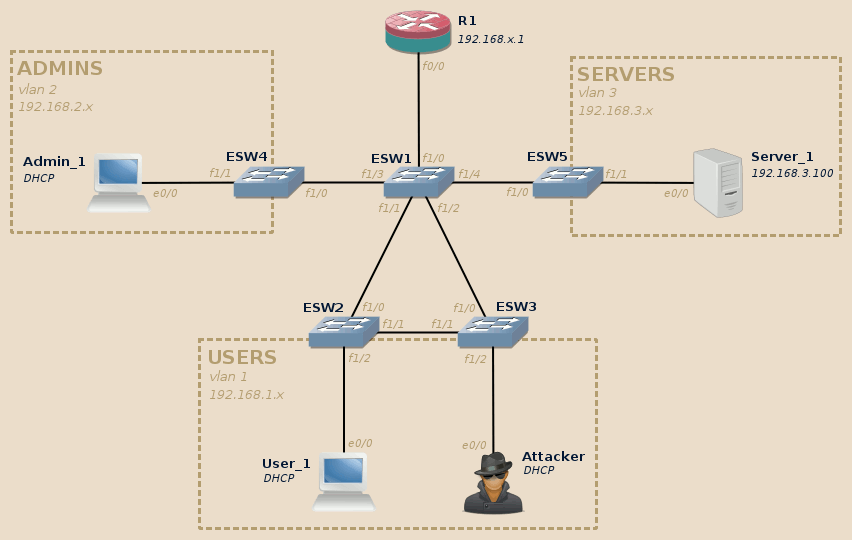
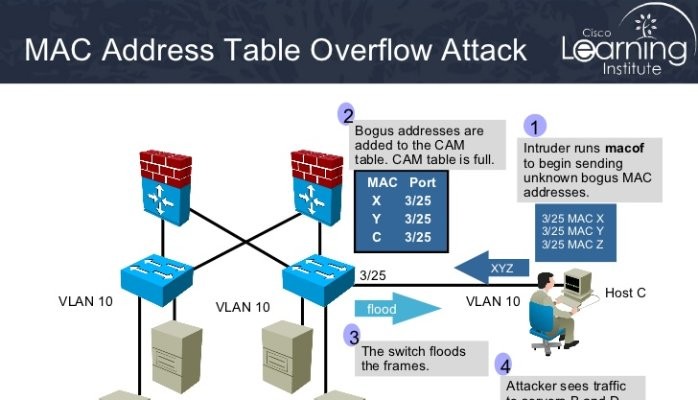
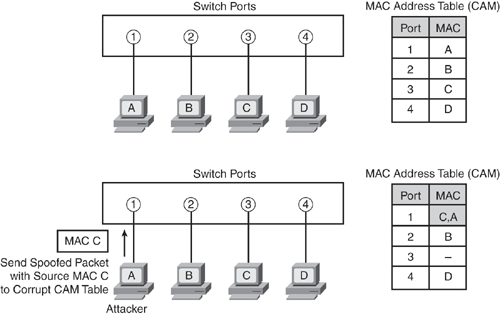
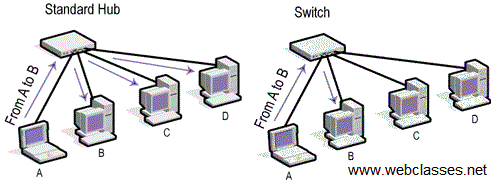
How to run a CAM Table Overflow attack in GNS3 using Cisco 3725 routers? - Network Engineering Stack Exchange

Switch Security: Management and Implementation (2.2) > Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration | Cisco Press