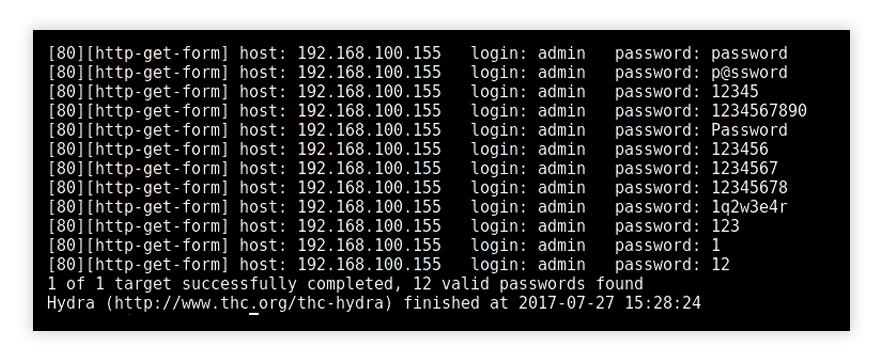
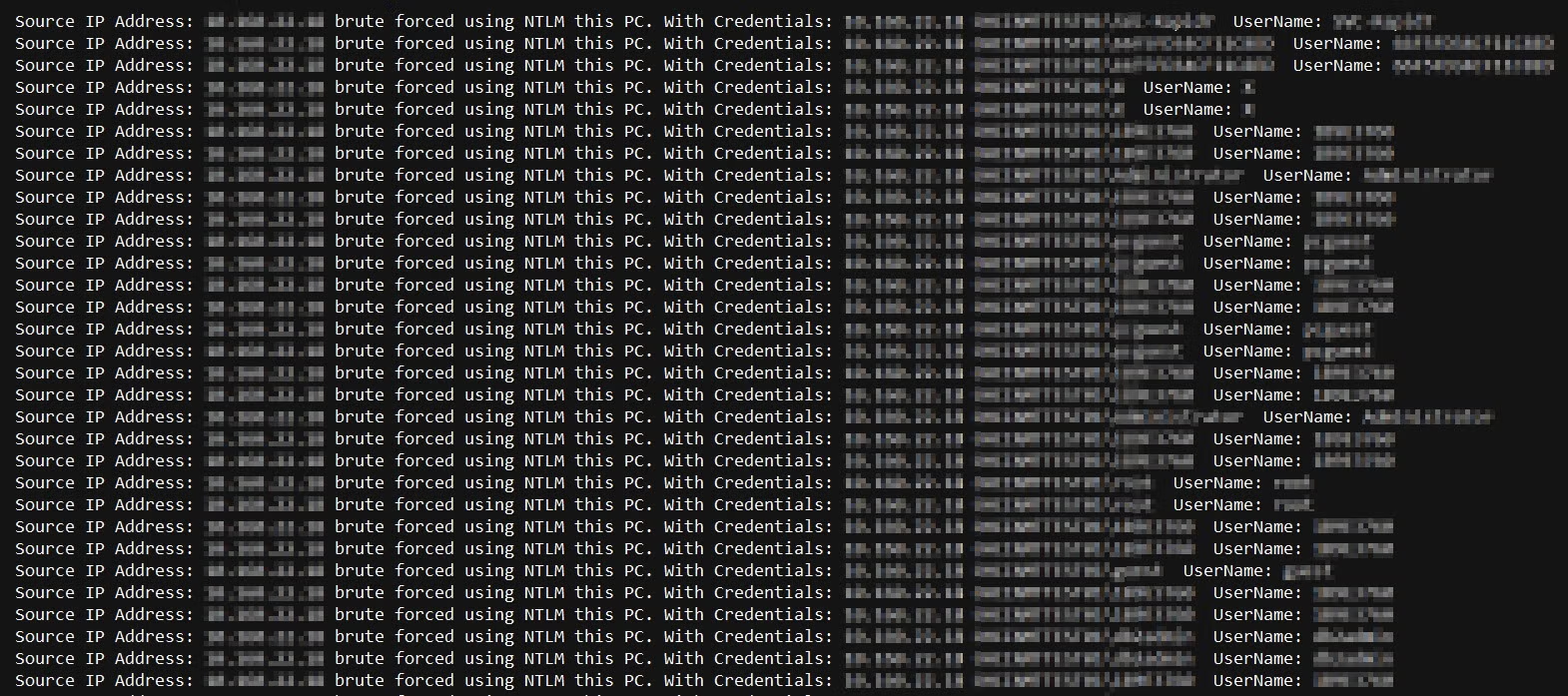
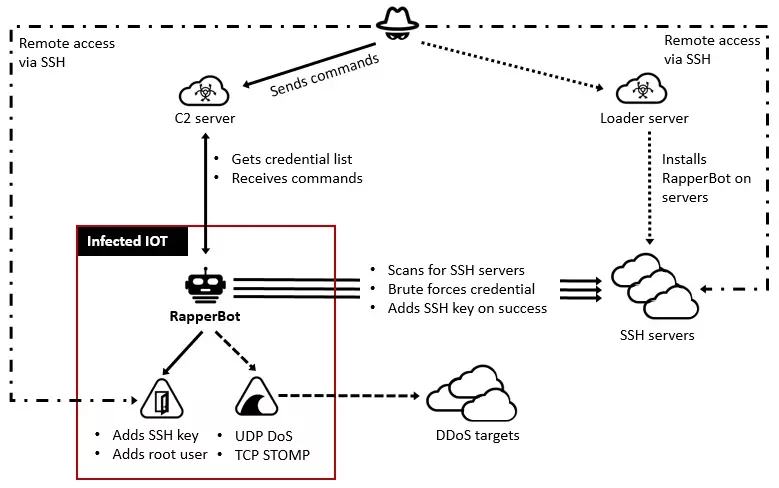
security - What should I do about someone trying to brute force attempt to login to our SQL Server 'sa' account? - Server Fault
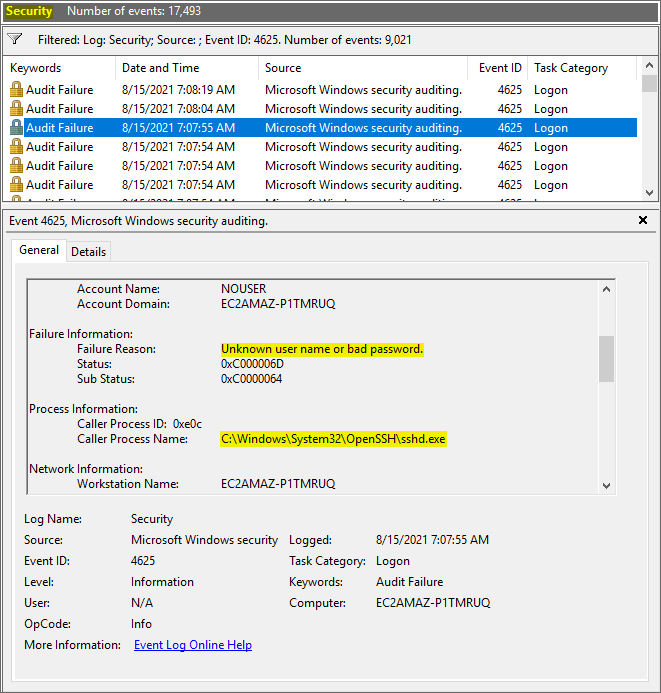
OpenSSH Brute-Force Protection - How to stop brute-force attacks on SSH protocol on Windows. OpenSSH protection on Windows.
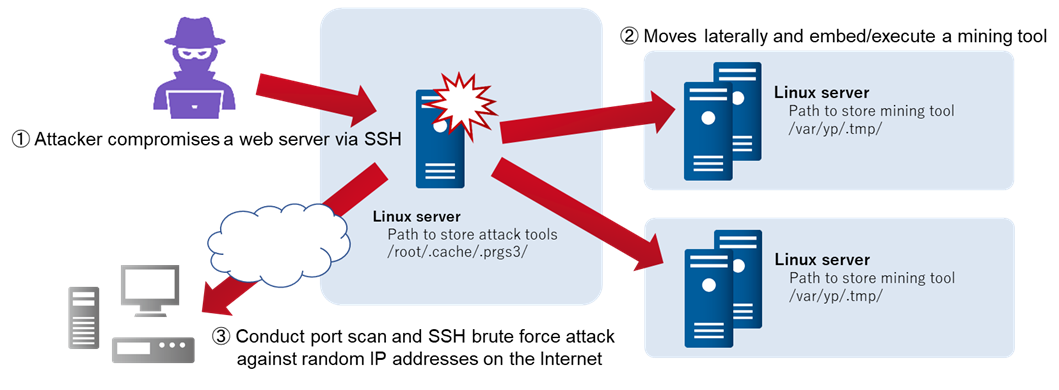





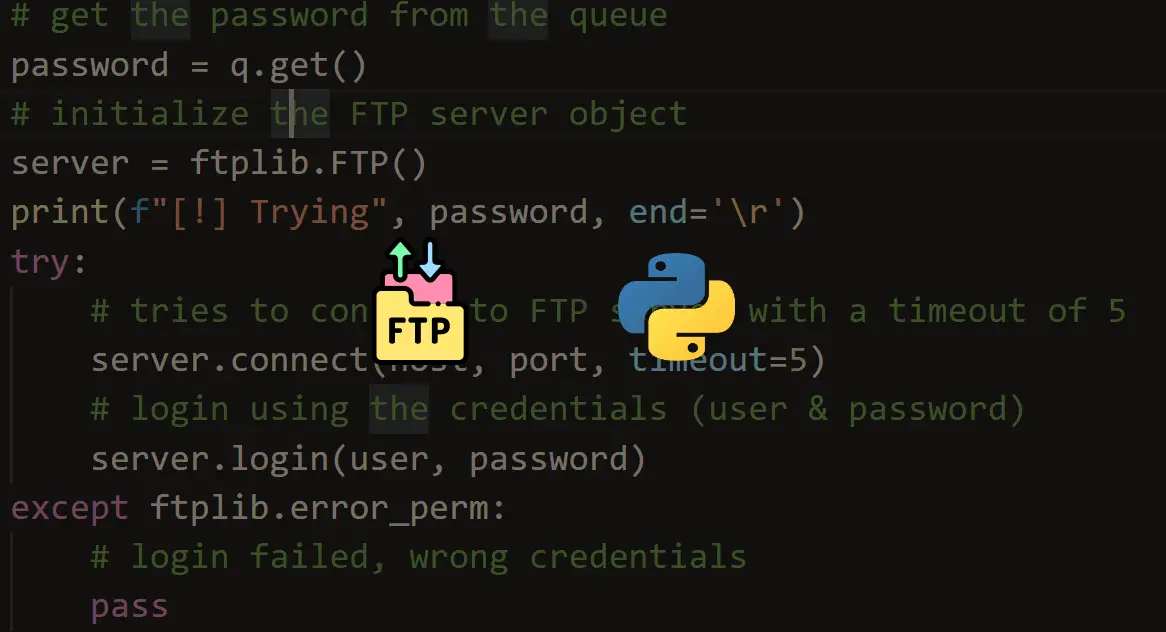
![Brute-Forcing FTP Credentials for Server Access [Tutorial] - YouTube Brute-Forcing FTP Credentials for Server Access [Tutorial] - YouTube](https://i.ytimg.com/vi/hE_Kjav323U/maxresdefault.jpg)